Announcing record of remediation & audit logs in Puppet Remediate 1.3
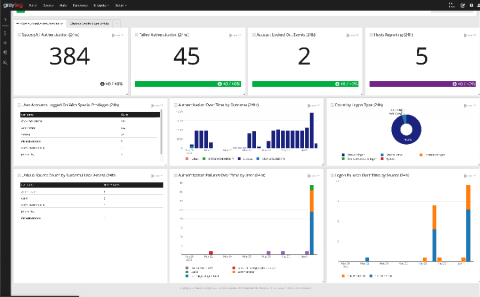
Today we are pleased to announce the release of Puppet Remediate 1.3.0. This release includes new features requested by our customers, including even more capabilities to help you track and trace network activity, and give you more control of the data in your dashboard. Read on for background and a look at the new capabilities.