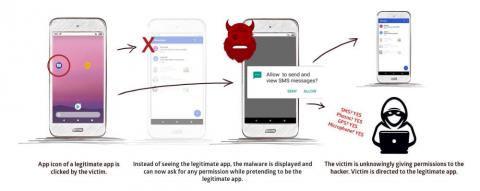
5 Best Security Practices for Tomcat Servers
Tomcat servers are widely used application servers for today’s development architectures, popular for hosting Java based applications. Below is a guide on best security practices for security your Tomcat Server environment. Banner grabbing is the process of gaining information from computer systems including services, open ports, version, etc. When sending a server host request via telnet command, you pass along the server name, port, and version.