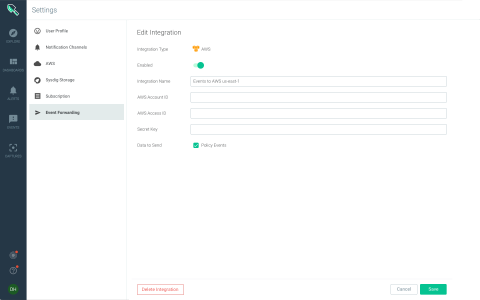
Sysdig Secure now integrates with AWS Security Hub
Today, Sysdig is proud to announce our integration with the AWS Security Hub. AWS Security Hub consolidates alerts and findings from multiple AWS services including, Amazon GuardDuty, Amazon Inspector, as well as from AWS Partner Network (APN) security solutions, which Sysdig is already a part of. This single pane of glass gives you a comprehensive view of high-priority security alerts and compliance status across AWS accounts.