Tigera adds eBPF support to Calico
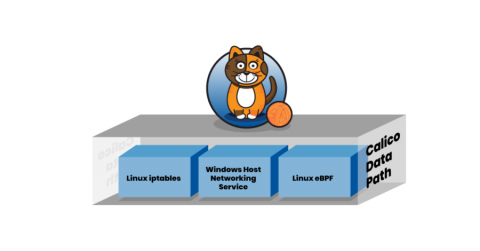
Calico provides users flexibility by detecting and choosing the right tool for the right job. One of our core values at Tigera is Our customer is the hero of our story. We consider the OpenSource users of Project Calico our customers and we intently listen to their needs to continuously deliver new capabilities and enhanced performance.