Now's the Time to Perfect Your Customer Experience
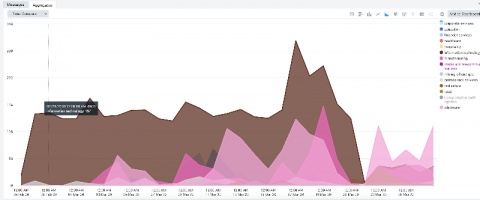
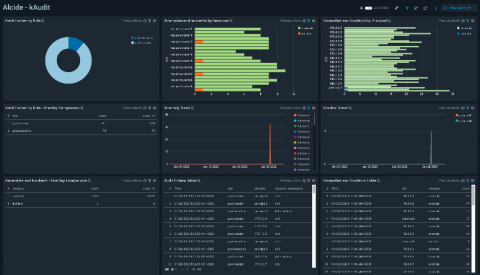
As the COVID-19 outbreak progressively impacts the world, many companies are grappling with the strain. It’s a very uncertain time for business right now. Even with so many factors out of your control, but there are a few things you can do proactively to protect your business. Keep your customers happy. Do everything you can to provide the best customer experience and remedy leaks early.