A Guide to Streamlined Troubleshooting with Intuitive Log Management Solutions
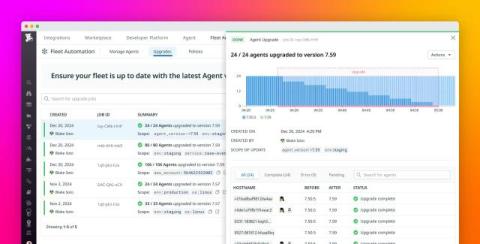
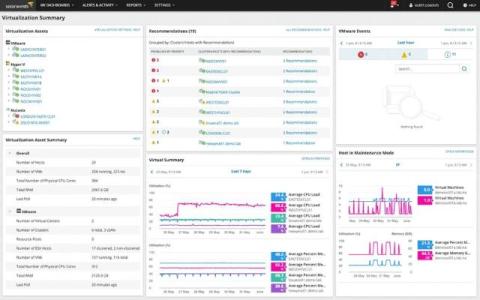
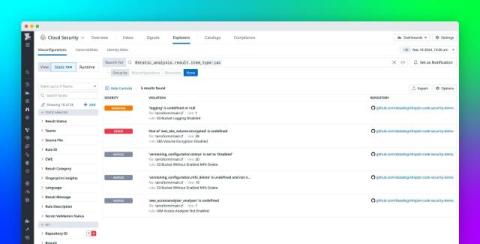
Efficient troubleshooting is a cornerstone of maintaining smooth operations in modern IT environments. Systems generate immense volumes of data, and sifting through logs without a structured approach can be challenging. Intuitive log management solutions simplify the process, helping IT teams quickly pinpoint issues and enhance system performance. This guide explores the key aspects of leveraging log management tools for seamless troubleshooting.