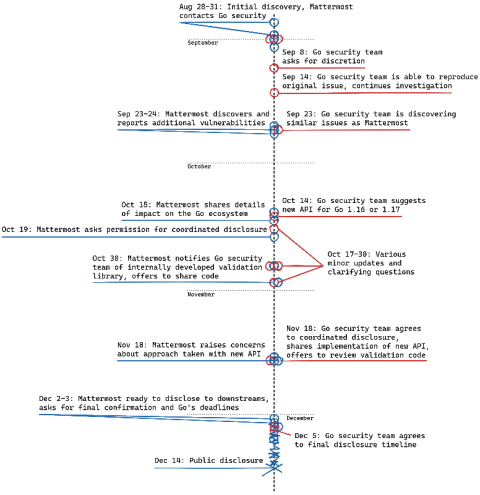
Speed Up Development with Automated Kubernetes Deployments
Are you or your team currently looking for your next-generation architecture? Or perhaps are you already there, but looking for the best way to automate and manage it. In this blog, we’re going to talk about deploying Rancher environments using the power of env0. Rancher is a complete software stack for teams adopting containers.