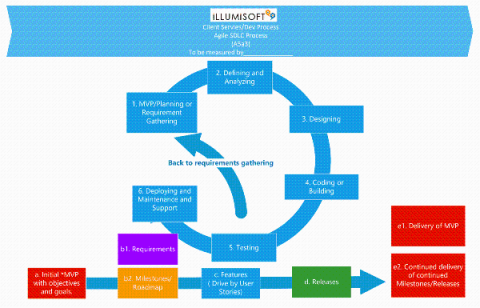
Using Splunk to Detect Sunburst Backdoor
TL;DR: This blog contains some immediate guidance on using Splunk Core and Splunk Enterprise Security to protect (and detect activity on) your network from the Sunburst Backdoor malware delivered via SolarWinds Orion software. Splunk’s threat research team will release more guidance in the coming week. Also please note that you may see some malicious network activity but it may not mean your network is compromised. As always review carefully.