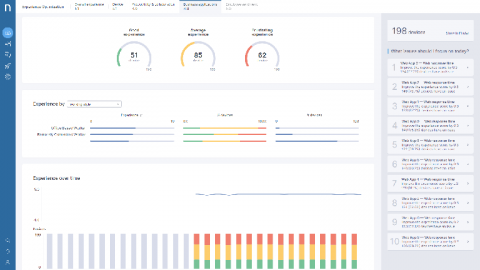
Nexthink Further Enhances UI for Experience Platform
In February 2020, Nexthink introduced its new design system, Apollo. While it unveiled some great new accessibility and design features, its true raison d’être was everything happening on the back-end, a powerful new design engine to scale and accelerate the roll-out of new features. Well, 6 months later and here we are. As promised, this latest round of enhancements offers several intuitive modifications to make IT’s life easier when supporting the Digital Employee Experience.