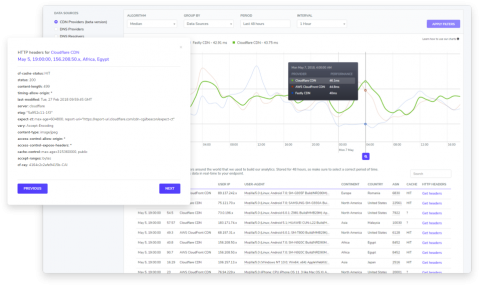
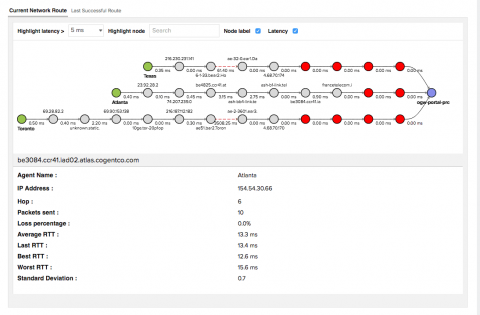
Is global expansion crippling your hold on network security?
Globalization and foreign investments have completely changed the way enterprises are run today. Enterprises are expanding geographically to diversify their risk portfolio, but this expansion hasn’t been linear. From mergers to buyouts, today’s enterprises have endless possibilities, which translates into inorganic, exponential growth—something that’s become the industry norm.