Operations | Monitoring | ITSM | DevOps | Cloud
Security
The latest News and Information on CyberSecurity for Applications, Services and Infrastructure, and related technologies.
The Latest Ransomware Stats Are In and It's Not Good News.
Out of 10 key metrics tracked quarterly to establish the state of ransomware activity, only one metric stayed static from Q1 to Q3 2022. The other nine all worsened. That’s an alarming trend, especially given that many business leaders hoped to see ransomware activity taper off after a historic surge during the peak of the pandemic. Ivanti, together with Cyber Security Works and Cyware, collaborated on the just-released report.
What Is Phishing?
Phishing is the fraudulent practice of manipulating people via emails, texts, websites or phone calls into disclosing sensitive information, like credit card numbers or login credentials, that can then be used to access and attack systems. Cybercriminals do this by tricking users into taking specific actions that cause them to inadvertently download malware.
Untangling Account Management With User Permissions
Companies, like most things, rarely grow in a straight line. Plants will take root where they can, and send shoots where they can to get the most sunlight, even if there are obstacles in the way. But vines and branches aren’t known for their efficient pathing, which can make a tangled mess of the whole plant. So get a good sun hat and some pruning shears ready; you’ll need them today! The difference between organic and structured growth is one of purpose and planning.
Jason Chan on Harnessing Security Automation to Manage Cyberthreat Complexity
Torq is extremely proud to have Jason Chan on our advisory board. Jason has more than 20 years of experience working in cybersecurity. He’s one of the world’s leading experts in adopting security automation, cloud security, and enhancing security in modern software development practices. Jason’s most recent career experience was leading the information security organization at Netflix for more than a decade.
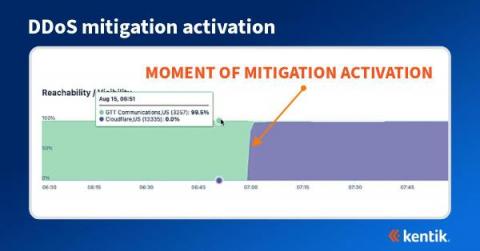
How BGP propagation affects DDoS mitigation
We often think of DDoS attacks as volumetric malicious traffic targeted against organizations that effectively take a service offline. Most frequently detected by anomalous behavior found in NetFlow, sFlow, IPFIX, and BGP data, what may not be well understood is how the DDoS mitigation works and how it’s possible to visualize the effectiveness of the mitigation during and after an attack.
How BGP propagation affects DDoS mitigation
Bridge Your Data Silos to Get the Full Value from Your Observability and Security Data
In my work as a technical evangelist at Cribl, I regularly talk to companies seeing annual data growth of 45%, which is unsustainable given current data practices. How do you cost effectively manage this flood of data while generating business value from critical data assets?
How Calico CNI solves IP address exhaustion on Microsoft AKS
Companies are increasingly adopting managed Kubernetes services, such as Microsoft Azure Kubernetes Service (AKS), to build container-based applications. Leveraging a managed Kubernetes service is a quick and easy way to deploy an enterprise-grade Kubernetes cluster, offload mundane operations such as provisioning new nodes, upgrading the OS/Kubernetes, and scaling resources according to business needs.
4 Website Security Threats (2022) + Solutions
For server administrators tasked with ensuring the reliable operation of their web applications, the thought of a lurking cyberattack can be one to lose sleep over. An attack on your system and the services you provide could render your web applications unresponsive. What’s worse, important information that depends on privacy and the careful storing of data is put at risk.