Operations | Monitoring | ITSM | DevOps | Cloud
Security
The latest News and Information on CyberSecurity for Applications, Services and Infrastructure, and related technologies.
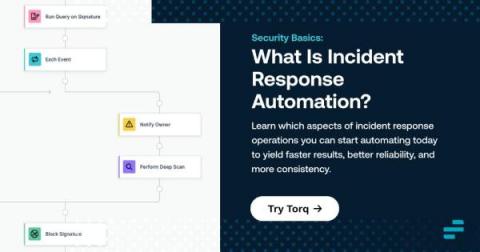
Security Basics: Incident Response and Automation
Incident response is one of the most challenging tasks that IT teams face. It's challenging not just because it typically involves many stakeholders and moving pieces, but also because teams usually face pressure to respond as quickly as possible. That's why investing in incident response automation is a wise choice. Although it may not be possible to automate every aspect of every incident response workflow, being able to automate at least the major elements of incident response will yield incident management processes that are faster, more reliable, and more consistent.Keep reading to learn about the components of incident response and which incident response activities to start automating.
Tips and Tricks for the Small SOC: Part II
It’s Cybersecurity Awareness Month, and in that spirit, we’re offering a number of tips and tricks small security operations center (SOC) teams can use. I started my career working as part of a small SOC team, and working with other security experts here at Logz.io, we’re happy to offer these to small SOC teams who can often use all the help they can get! In the last post, we talked about managing security talent and building processes.
New Vulnerability Scanning Features in Tanzu Application Platform 1.3
What is confidential computing? A high-level explanation for CISOs
Privacy enhancing technologies and confidential computing are two of my favorite topics to talk about! So much so that I am writing this blog post on a sunny Saturday afternoon. But wait, what’s that I hear you murmuring? “What is confidential computing? And how does it affect me?” Those are two very good questions.
To Thrive in the Everywhere Workplace, IT and Security Teams Need to Work Together
It’s Cybersecurity Awareness Month. For a CIO, this is like the holidays, and there’s lots to celebrate and lots to do. By reading this, you’re helping me check something off my list: I want everyone in the IT and security landscape to know how these two teams can work together for a more efficient, productive and secure enterprise. To those outside the departments, IT and security teams are often conflated.
Share secrets with standalone projects with project context restrictions
Introducing project context restrictions for GitLab organizations. This feature enables project-based restrictions on contexts for standalone projects that are not tied to a VCS. Standalone projects are available at this time only with a GitLab integration with CircleCI. In this blog post, we hope to explain the value of this feature and how it can be used to further secure your workflows.
Understanding the Different IT Security Certifications
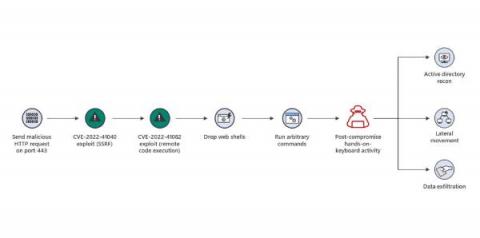
Microsoft Zero-Day Exchange Exploits Show Value of Network Behavior Visibility
There is no end to zero-day attacks. Lessen the pain by spotting them early. In recent days two zero-day vulnerabilities against Microsoft on-premises Exchange Servers have been publicized and exploited. The good news is that Exchange cloud users such as Microsoft 365 customers, need not worry as these exploits are only against the on-premises versions.
Keeping Your Organization Secure with Limited SOC Resources
Organizations face a growing threat from cybercriminals while struggling to find qualified security professionals who can protect their infrastructure and sensitive data. This blog will explore the concept of a Security Operations Center (SOC) and the role of SOC analysts in securing your organization. We will also discuss how your organization can leverage automation to improve SOC effectiveness and fill in the gaps when you cannot support a full staff of security professionals.