Operations | Monitoring | ITSM | DevOps | Cloud
Security
The latest News and Information on CyberSecurity for Applications, Services and Infrastructure, and related technologies.
The State of Security Data Management in 2022
Today, Cribl is releasing The State of Security Data Management 2022 in collaboration with CITE Research. The report examines the challenges that enterprises are facing as they work to balance evolving business priorities with cyber threats. The report was conducted in September 2022 and surveyed 1,000 senior-level IT and security decision-makers. The survey found that, although most organizations are confident in their data management strategy, few believe it’s actually sustainable.
Three ways to encourage the importance of security posture
“I’m not a big enough business… I’m too small… no one will want to hack me.” “I don’t have anything of any importance that anyone would want… I’m not terribly concerned.” “It hasn’t happened to us yet, so it isn’t something I’m worried about.” “What you’re proposing seems like overkill to me. And besides, we don’t have the extra funds in our budget anyway.
What Is Phishing? Insider Risk & How to Prevent It
How To Properly Protect Your Intelectual Property On The Internet
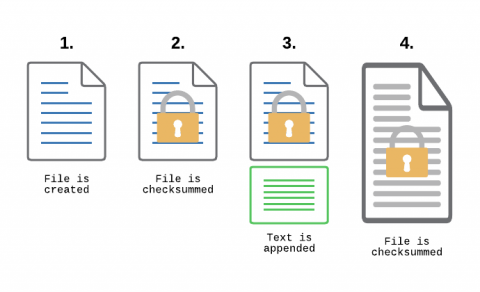
Monitoring Transaction Log Files for PCI compliance
File Integrity Monitoring, aka as FIM, is a must-have feature for anyone in charge of security. With FIM, one can detect when a critical file, such as a file that belongs to the Operating System, or a key configuration file, is changed. In most cases, configuring FIM is straightforward: If the file changes then generate an alert.
Accessing CFEngine nightly packages
Did you know that nightly builds of CFEngine are available? cf-remote is the most convenient way to get nightly packages. If you’re not familiar with it, or if you need a refresher, check out our other blog posts about cf-remote.
Checkly Completes SOC 2 Type 1 Audit
A Service Organization Control (SOC) audit is one of the most extensive tests an organization can undergo to demonstrate the ongoing maintenance of high-level information security. Today, we’re thrilled to announce that Checkly is SOC 2 Type 1 compliant after completing a successful audit by an accredited auditing firm. This demonstrates that Checkly’s information security policies, procedures, and practices meet the SOC 2 guidelines for security and data privacy.