Operations | Monitoring | ITSM | DevOps | Cloud
Security
The latest News and Information on CyberSecurity for Applications, Services and Infrastructure, and related technologies.
PCI DSS - Requirements and Levels of Compliance
The security of payments is underlined in multiple visuals we confront each day while visiting numerous websites and apps. Can businesses and customers benefit from that? Any company handling cardholder data, whether a startup or an enterprise, must adhere to the Payment Card Industry Data Security Standard (PCI DSS). You must validate your compliance annually in order to remain compliant.
Three Ways a Proactive Defense Strategy Can Prevent Cyberattacks
Cloud certifications for the security of your data
More and more companies around the world are using cloud solutions to run their applications, software or to store their data. But what about cloud compliance? The democratisation of the cloud is not surprising as it provides access to virtual data storage where companies no longer need to buy or maintain their own IT infrastructure. However, with cloud solutions, the security of user data should not be overlooked. There are cloud certifications and regulations that can help you in your choice.
Making Sure the Future of Federal Work Is Secure and Enjoyable - Why We're Partnering with NIST on Its Zero Trust Project
Last year, we announced our partnership with the National Cybersecurity Center of Excellence (NCCoE) at the National Institute of Standards and Technology (NIST) to work on the Implementing a Zero Trust Architecture project. After a year of collaboration with its industry partners, including Ivanti, NIST recently released its preliminary draft, NIST Cybersecurity Practice Guide SP 1800-35 Vol B, for public comment.
Code signing: securing against supply chain vulnerabilities
When creating an application, developers often rely on many different tools, programs, and people. This collection of agents and actors involved in the software development lifecycle (SDLC) is called the software supply chain. The software supply chain refers to anything that touches or influences applications during development, production, and deployment — including developers, dependencies, network interfaces, and DevOps practices.
What Are Red Team Scenarios? Methodology and Examples
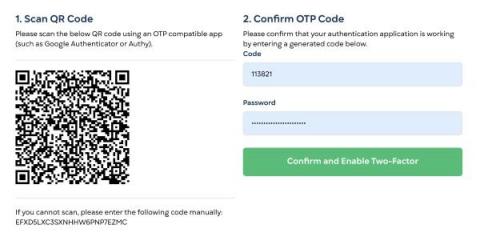
Protect your StatusGator Account with Two-Factor Auth
StatusGator now supports Two-Factor Authentication, often called 2FA, a more secure way of signing into your account. Using an authenticator app such Google Authenticator, Authy, or a password manager like 1Password, you can now protect your StatusGator account with a second authentication factor, a one-time password (OTP) that you enter after signing in.
Is Cybersecurity Hard? The Basics Made Easy To Understand
SOC 2 Compliance - What is it?
In today's world, information security is a noteworthy concern for all organisations, including those outsourcing vital enterprise operations to third parties. Enterprises are vulnerable to data theft, extortion, and malware installation when mishandled data, particularly by application and network security providers. American Institute of Certified Public Accountants (AICPA) was the organization that created SOC 2 which stands for ‘Service Organization Control 2'.