Operations | Monitoring | ITSM | DevOps | Cloud
Security
The latest News and Information on CyberSecurity for Applications, Services and Infrastructure, and related technologies.
5 Secure Remote Access Solutions for Businesses
As many workers have shifted to working in offsite locations, the need for secure remote access for remote support and device management has never been greater. IT teams need It can be difficult to securely access and control all your organization’s endpoints, but secure remote access solutions simplify and streamline that process.
CFEngine Build in Mission Portal Web UI (Developer demo)
SOC 2: Data Security For Cloud-Based Observability
As more companies adopt SaaS services over on-premise delivery models, there is a natural concern around data security and platform availability. Words on a vendor’s website can provide insights to prospective customers on the process and policies that companies have in place to alleviate these concerns. However, the old adage of “actions speak louder than words” does apply. Trust in a website’s words only goes so far.
Zero Trust Security: Key Concepts and 7 Critical Best Practices
Zero trust is a security model to help secure IT systems and environments. The core principle of this model is to never trust and always verify. It means never trusting devices by default, even those connected to a managed network or previously verified devices. Modern enterprise environments include networks consisting of numerous interconnected segments, services, and infrastructure, with connections to and from remote cloud environments, mobile devices, and Internet of Things (IoT) devices.
How To Build Cybersecurity Culture At Your Company
Cybersecurity is a key priority for small, medium, and large companies. If you are a keen internet user or a lover of news and trending topics, I am sure you already know the current threats surrounding the cybersecurity realm. Cybersecurity threats are now a nightmare that faces all levels of organizations. Malware attacks, DDoS threats, phishing, brute force, SQL injections, etc. are running riot in the internet streets.
Thinking Smarter About M&A-Are you secure?
With the continued focus in our space on the movement from MSP to MSSP, it’s crucial to remember that products alone don’t necessarily make you an MSSP. For smaller customers, although you might be able to provide a range of security solutions (like EDR and backup) and compliment these with an RMM to provide insight and control over end user devices, this is not enough to call yourself an MSSP.
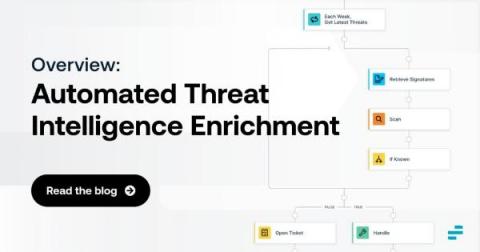
Automated Threat Intelligence Enrichment: An Overview
Discovering security threats is good and well. But, in many cases, simply knowing that a threat may exist is not enough. Instead, you also need threat intelligence enrichment. Threat enrichment plays a critical role in helping to evaluate and contextualize threats, root out false positives and gain the insights necessary to mitigate risks as efficiently and quickly as possible.
What Is a Secure SDLC?
The Software Development Lifecycle (SDLC) framework defines the entire process required to plan, design, build, release, maintain and update software applications, including the final stages of replacing and decommissioning an application when needed. A Secure SDLC (SSDC) builds on this process, integrating security at all stages of the lifecycle. When migrating to DevSecOps (collaboration between Development, Security, and Operations teams), teams typically implement an SSDLC.
Processes, forks and executions - part 1
While working on the integration of CFEngine Build into Mission Portal we came to the point where we needed to start executing separate tools from our recently added daemon - cf-reactor. Although it may seem like nothing special, knowing a bit about the process creation and program execution specifics (and having to fight some really hard to solve bugs in the past) we spent a lot of time and effort on this step.