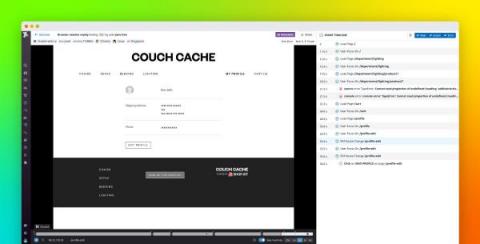
Obfuscate user data with Session Replay default privacy settings
Session Replay enables you to replay in a video-like format how users interact with your website to help you understand behavioral patterns and save time troubleshooting. Visibility into user sessions, however, can risk exposing sensitive data and raise privacy concerns. For example, a user session may include typing in a credit card or social security number into an input field.