Operations | Monitoring | ITSM | DevOps | Cloud
Security
The latest News and Information on CyberSecurity for Applications, Services and Infrastructure, and related technologies.
Are You Spending Enough on Cybersecurity?
Cybercriminals do not discriminate against the organization, people or industry they target. These actors look to exploit vulnerabilities in resources to intercept valuable data from small and medium-sized businesses (SMBs). Cyberattacks are inevitable, and organizations must have the right controls and information security systems to mitigate the impact of an attack.
Humans Can be Hacked. So Stop Using Passwords, Already!
Humans are the weakest link in the cybersecurity chain. Where have you heard that before? Humans can be hacked! That too? Yes, I am also one of those weak links in the constant battle against malicious cyber criminals and it can be attributed to just being lazy. It’s human nature and we can easily be socially engineered into giving up our precious online user credentials to the bad guys.
5 Automated Anti-Phishing Protection Techniques
In an age when attackers create over a million phishing sites each month, and phishing serves as a beachhead for 95 percent of all attacks against enterprise networks, how can businesses respond? Part of the answer lies in educating users to recognize and report phishing, of course. But user education only goes so far – particularly because the same statistics cited above show that, on average, only 3 percent of users will report phishing emails.
The number one business bad habit MSPs need to stop doing immediately
The N-able Head Security Nerd, Lewis Pope, just published a blog outlining the top 25 cybersecurity bad practices demonstrated by MSPs today. To accompany his post, I wanted to add one more risky bad habit to his list. It’s something I commonly see being practiced by too many MSPs from a business perspective—allowing a customer’s budget to dictate what a cybersecurity offering should look like.
25 cybersecurity bad practices: more than just bad habits
The CISA (Cybersecurity & Infrastructure Security Agency) recently started an initiative to create a catalogue of exceptionally risky cybersecurity bad practices. While this will be a welcome and very useful tool once it is complete, only two practices are currently listed. Since cybersecurity and business decisions can be time-sensitive, we wanted to expand on the CISA’s list.
How to Schedule Patching for Security Event Manager
Interview with Cybersecurity Specialist Mark Kerzner
For the newest instalment in our series of interviews asking leading technology specialists about their achievements in their field, we’ve welcomed Mark Kerzner, software developer and thought leader in cybersecurity training who is also the VP at training solutions company, Elephant Scale. His company has taught tens of thousands of students at dozens of leading companies. Elephant Scale started by publishing a book called ‘Hadoop Illuminated‘.
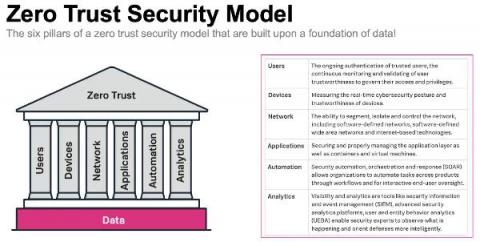
A Zero Trust Security Approach for Government: Increasing Security but also Improving IT Decision Making
Public sector organisations are in the middle of a massive digital transformation. Technology advances like cloud, mobile, microservices and more are transforming the public sector to help them deliver services as efficiently as commercial businesses, meet growing mission-critical demands, and keep up with market expectations and be more agile.