Operations | Monitoring | ITSM | DevOps | Cloud
Security
The latest News and Information on CyberSecurity for Applications, Services and Infrastructure, and related technologies.
SSL certificates monitoring
SSL is an acronym for Secure Sockets Layer. It's considered as a standard security technology, it serves as an Internet protocol by establishing an encrypted link between a browser and a web server. SSL is used to secure credit card transactions, data transfer and logins thereby preventing hackers from accessing private data.
What is the MITRE ATT&CK Framework for Cloud? | 10 TTPs You should know of
In any case, by using the MITRE ATT&CK framework to model and implement your cloud IaaS security, you will have a head start on any compliance standard since it guides your cybersecurity and risk teams to follow the best security practices. As it does for all platforms and environments, MITRE came up with an IaaS Matrix to map the specific Tactics, Techniques, and Procedures (TTPs) that advanced threat actors could possibly use in their attacks on Cloud environments.
How to mitigate CVE-2021-33909 Sequoia with Falco - Linux filesystem privilege escalation vulnerability
The CVE-2021-33909, named Sequoia, is a new privilege escalation vulnerability that affects Linux’s file system. It was disclosed in July, 2021, and it was introduced in 2014 on many Linux distros; among which we have Ubuntu (20.04, 20.10 and 21.04), Debian 11, Fedora 34 Workstation and some Red Hat products, too. This vulnerability is caused by an out-of-bounds write found in the Linux kernel’s seq_file in the Filesystem layer.
Securing XML implementations across the web
In December 2020, we blogged about security issues in Go’s encoding/xml with critical impact on several Go-based SAML implementations. Coordinating the disclosure around those issues was no small feat; we spent months emailing the Go security team, reviewing code, testing and retesting exploits, coming up with workarounds, implementing a validation library, and finally reaching out to SAML library maintainers and 20 different companies downstream.
Malware alert: The RedXOR and Mamba attacks and how to defend against them
Picture this: It’s a normal day of working from home as usual since the COVID-19 outbreak. After that satisfying cup of coffee, you log in. But something is wrong. No matter how many times you click, your files don’t open. Your screen is frozen and refuses to budge. And then, you see one of the worst nightmares any IT admin can imagine: “Oops, your files have been encrypted. But don’t worry, we haven’t deleted them yet.
Collecting and operationalizing threat data from the Mozi botnet
Detecting and preventing malicious activity such as botnet attacks is a critical area of focus for threat intel analysts, security operators, and threat hunters. Taking up the Mozi botnet as a case study, this blog post demonstrates how to use open source tools, analytical processes, and the Elastic Stack to perform analysis and enrichment of collected data irrespective of the campaign.
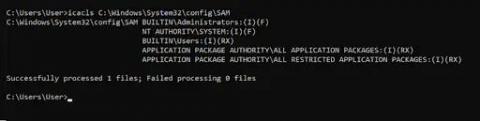
Detecting SeriousSAM CVE-2021-36934 With Splunk
SeriousSAM or CVE-2021-36934 is a Privilege Escalation Vulnerability, which allows overly permissive Access Control Lists (ACLs) that provide low privileged users read access to privileged system files including the Security Accounts Manager (SAM) database. The SAM database stores users' encrypted passwords in a Windows system. According to the Microsoft advisory, this issue affects Windows 10 1809 and above as well as certain versions of Server 2019.
What's new in Sysdig - July 2021
Welcome to another monthly update on what’s new from Sysdig! Happy 4th of July to our American audience, and bonne Bastille to our French friends. It’s been heating up in the northern hemisphere, so we hope you’ve all been managing to stay cool and safe. Our team continues to work hard to bring great new features to all of our customers, automatically and for free! The big news this month is our intent to acquire Apolicy, which has everyone full of excitement.