DarkSide Ransomware: Splunk Threat Update and Detections
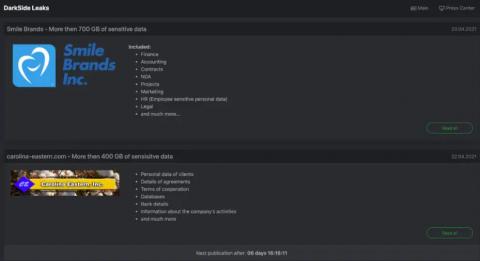
The ransomware campaign against the Colonial Pipeline highlights the dangers and real-life consequences of cyberattacks. If you want to understand how to use Splunk to find activity related to the DarkSide Ransomware, we highly recommend you first read “The DarkSide of the Ransomware Pipeline” from Splunk’s Security Strategist team. In short, according to the FBI, the actors behind this campaign are part of the “DarkSide” group.