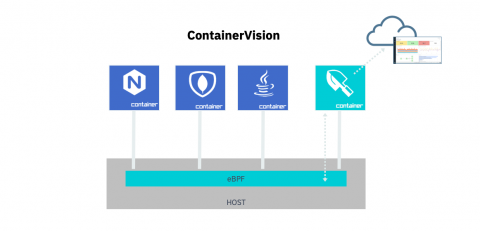
Introducing container observability with eBPF and Sysdig.
Today we’ve announced that we’ve officially added eBPF instrumentation to extend container observability with Sysdig monitoring, security and forensics solutions. eBPF – extended Berkeley Packet Filter – is a Linux-native in-kernel virtual machine that enables secure, low-overhead tracing for application performance and event observability and analysis.