Operations | Monitoring | ITSM | DevOps | Cloud
%term
Configuring an effective incident management process
Five worthy reads: Fend off cyberattacks using dark web intelligence
Five worthy reads is a regular column on five noteworthy items we’ve discovered while researching trending and timeless topics. This week, we discuss how organizations can use the dark web to build a treasure trove of actionable intelligence to prevent attacks.
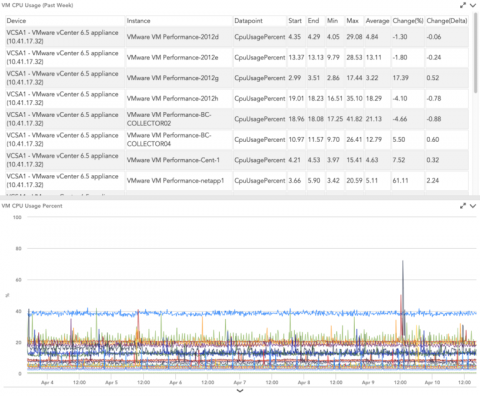
Viewing LogicMonitor Reports Within Dashboards
As a Sales Engineer, I hear interesting product requests on a daily basis, and integrating LogicMonitor reports with LogicMonitor dashboards comes up frequently. LogicMonitor's reporting engine has many useful functions from capacity planning to SLA calculation, and dashboards help users visually digest the raw data of reports.
Monitorama 2019 - Portland, Oregon
A few members of the Scout team had the chance to head to Monitorama in Portland, Oregon this week. For those who do not know what Monitorama is, it is a 3-day, open-source monitoring conference with a single track. There is plenty of time during the breaks to chat with attendees, ask the speakers questions or just catch up on some email.
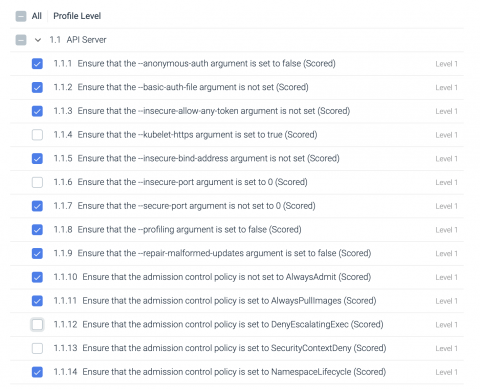
Custom compliance filters with Sysdig Secure
Custom compliance filters is now GA as part of the SaaS and on-prem release. With Sysdig Secure, enterprises can enforce compliance filters across the container lifecycle. Teams can automate regulatory compliance controls for PCI, NIST, CIS, for Kubernetes and container environments at scale.They also gain visibility into the performance, health, compliance, and security posture of an on-prem and/or multi-cloud environment from a single dashboard.
Production-Grade Ingress Solution Using Citrix and Rancher
This post outlines how to build a production-grade ingress solution using Citrix ADC on Rancher. Customers can confidently expose end user traffic to microservices or legacy workloads on Kubernetes clusters on Rancher using this solution.
Enhance Cloud Operations and Productivity with Mesosphere DC/OS 1.13
Istio and Kubernetes in production. Part 2. Tracing
In the previous post, we took a look at the building blocks of Service Mesh Istio, got familiar with the system, and went through the questions that new Istio users often ask. In this post, we will look at how to organize the collection of tracing information over the network.
Automating Collection of Troubleshooting Data with Triggers: a How-To Guide
Everyone wants to be more efficient — to spend less time on the tedious things, and more time on the things that move the needle. As much as possible, if you can automate those tedious things, you should. With Honeycomb, we enable you to understand how your application behaves in production through the ability to iteratively ask questions of the system instrumentation data, no matter how granular. Honeycomb triggers enable you to be notified when specific things happen in your system.