Operations | Monitoring | ITSM | DevOps | Cloud
Zero Trust
Implementing Zero Trust: A Practical Guide
The Landscape of Zero Trust Adoption: Insights from Our 2023 Zero Trust Progress Report
Organizations are responding to the changing cybersecurity landscape. And zero trust is at the heart of this change, with 68% of respondents saying they’re planning or actively working towards adopting a zero trust access model. In collaboration with Cybersecurity Insiders, Ivanti surveyed 421 US-based IT and cybersecurity professionals to identify the latest enterprise adoption trends, challenges, gaps and solution preferences related to zero trust security.
Understanding Zero Trust Principles
Have you ever wondered how to keep your digital assets truly secure in a world where cyber threats seem to evolve quicker than cybersecurity measures? If so, you might want to consider adopting a Zero Trust security model. Far from being a buzzword, Zero Trust has emerged as a holistic approach to cybersecurity that operates on a straightforward principle: “Never Trust, Always Verify”.
Modernizing the Air Force: DAFITC 2023
D2iQ is excited to be participating in the Department of the Air Force Information Technology and Cyberpower (DAFITC) 2023, in Montgomery, Alabama, from August 28-30. The theme of this year’s DAFITC conference is “Digitally Transforming the Air & Space Force: Investing for Tomorrow’s Fight.” Digital transformation of the Air Force and Space Force is part of a wider modernization effort that is accelerating across all U.S.
An Insider Look at Zero Trust with GDIT DevSecOps Experts
As cyber attacks have become ever more sophisticated, the means of protecting against cyber attacks have had to become more stringent. With zero trust security, the model has changed from “trust but verify” to “never trust, always verify.” Joining D2iQ VP of Product Dan Ciruli for an in-depth discussion of zero trust security was Dr. John Sahlin, VP of Cybersolutions at General Dynamics Information Technology (GDIT), and David Sperbeck, DevSecOps Capability Lead at GDIT.
Zero Trust: An Analyst's Perspective with Forrester Analyst, Steve Turner
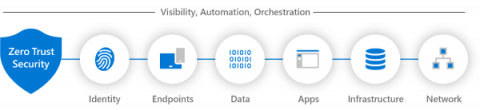
Mastering Zero Trust - Pillars for Security
Why Trust Zero Trust Ep. 16
Applying Zero Trust to Data Centre Networks
Zero trust isn’t an approach that can be delivered by buying a single product that claims to provide it. Instead, it is an approach that needs to be understood and implemented in complementary ways across an organization’s IT systems. We recently hosted a webinar titled Applying Zero Trust to Data Centre Networks to provide guidance on how organizations can use zero trust to enhance the security of their IT systems. The webinar details are below, after a summary of the topics covered.