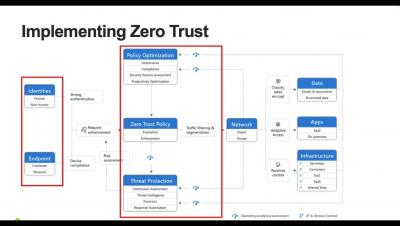
What is Zero Trust Security and Why Should You Care?
Automation has become a game changer for businesses seeking efficiency and scalability in a rather unclear and volatile macroeconomic landscape. Streamlining processes, improving productivity, and reducing incidence for human error are just a few benefits that automation brings. However, as organizations embrace automation, it’s crucial to ensure modern security measures are in place to protect these new and evolving assets.