Operations | Monitoring | ITSM | DevOps | Cloud
%term
CFEngine 3.13.0 released
Today we are very happy to announce the release of CFEngine 3.13.0. This is a non-LTS release, introducing new features and functionality. There is a lot happening with CFEngine these days! This release is closely following last weeks release of CFEngine 3.10.5 LTS, and soon we will also release the next patch version of our 3.12 LTS series. So keep following our updates!
v4 Training - Building Enterprise Application Dashboards
Icinga X.509 Module
We are pleased to announce the first open source release of our X.509 module for Icinga. The X.509 module for Icinga keeps track of certificates as they are deployed in a network environment. It does this by scanning networks for TLS services and collects whatever certificates it finds along the way. The certificates are verified using its own trust store.
Discover how to set up a Raspberry kiosk mode
If you’ve been shopping recently, you may or may not have seen stores and shops with screens, promotional videos, product images, statistics, etc. Normally, for this purpose the computers are hidden. These computers have immense power consumption, being on all day just to show something on the screen.
CloudHedge at AWS re:Invent 2018
AWS re:Invent 2018, one of the biggest cloud events of the year is less than a week away and we are all super excited to attend it. In its 7th edition this year, around 40,000+ attendees are expected in Las Vegas to attend dozens of keynotes, sessions, and workshops. With every passing year, AWS has come up with new technology and concepts that have modernized the grounds of the cloud ecosystem.
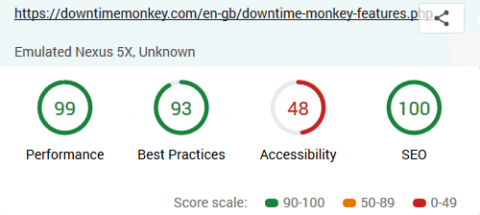
How we improved accessibility by 42% ...and how you can too!
We've just spent several days improving the accessibility of the Downtime Monkey website. Last week we carried out an audit of the site with Google's new tool web.dev, which is currently in beta. The tool returned high scores for three of the four aspects that were tested: performance (i.e. website speed), best practices and SEO (i.e. optimisation for search engines).
Icinga Web 2.6.2 Bugfix Release
We are happy to announce a new bugfix release for Icinga Web 2. Official packages are available on packages.icinga.com. Community repositories might need a while to catch up.
Site24x7 joins forces with Microsoft Teams to enable intelligent DevOps
Fantastic Data Breaches (and how to defend against them)
The retail world is under attack. Hackers across the globe are stealing personal details – including credit card information – on an alarmingly regular basis. This is done by placing digital “credit card skimmers” on compromised e-commerce sites. Hackers are able to access these sites usually through 3rd parties software in the form of JavaScript. Major retailers are prime targets – they are not immune and it’s a becoming a BIG problem for everyone.