Operations | Monitoring | ITSM | DevOps | Cloud
%term
A beginner's guide to scaling DevOps
Over the years “DevOps” has become quite the buzzword. It’s been used to describe culture changes, automation, change management, continuous delivery… essentially, a culture where dev and ops collaborate to build a faster, more reliable release pipeline.
ManageEngine Strengthens Endpoint Security with Patch Management on Cloud
Organizations Can Protect Against 4,000 Cyberattacks for Less Than a Dollar per Device per Month.
New Feature: Rate Limit SMS Alerts
We've just rolled out a brand new feature: the ability to set rate limits on SMS alerts. Before we tell you all about it, a big thank you to everyone who has provided feedback or submitted feature requests - it helps us focus on making the improvements that people really want.
Back to Basics: Working with Linux Audit Daemon Log File
If you run the audit daemon on your Linux distribution you might notice that some of the most valuable information produced by auditd is not transmitted when you enable syslog forwarding to Graylog. By default, these messages are written to /var/log/audt/audit.log, which is written to file by the auditd process directly and not sent via syslog.
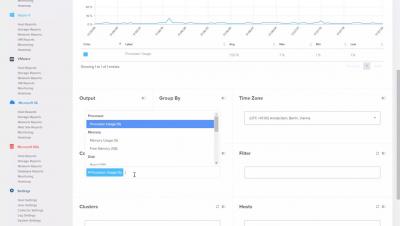
What's New In Grafana v5.0
Automation for the AWS platform - gain monitoring insight and automatically execute actions
As you probably know, Site24x7's AWS monitoring capabilities provide complete visibility into resource utilization and performance for key compute resources, storage, and database services powering your application in the Amazon Web Services (AWS) cloud. From here on out, you'll have the power to not only identify issues that might affect application performance, but also automatically invoke operational tasks across multiple AWS resources to resolve them quickly.
Reports
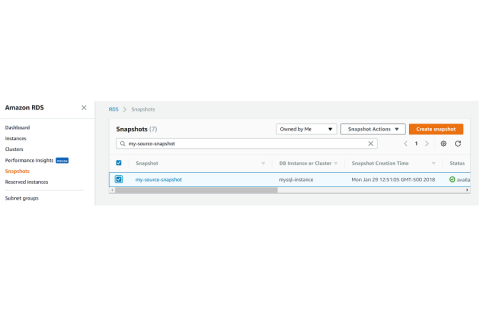
Copying RDS Snapshots Between Regions
In our previous posts, I showed you how to copy your DB and Aurora snapshots to ensure they are preserved beyond the lifetime of your RDS instance. However, those copies were simply second copies in the same region as the original. In this post, I’ll show you how to copy your RDS snapshots to a second region for extra protection. Please note that I will restrict this post to unencrypted snapshots. Copying encrypted snapshots is more involved, so I’ll show that in a separate post.
Icinga Monthly Snap January: Releases, Events and #icingalove
January brought us many releases, new cool Icinga Web 2 themes and news about upcoming events.