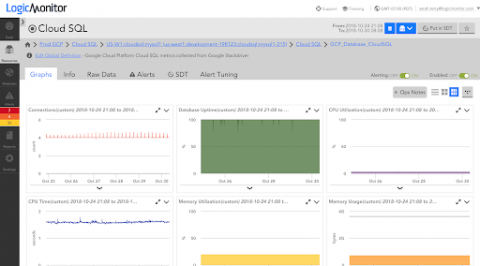
How to Monitor Google Cloud SQL
Google Cloud Platform’s (GCP) Cloud SQL is a managed MySQL and PostgreSQL database service. This service enables you to quickly set up and manage databases for your applications without having to maintain the underlying infrastructure.