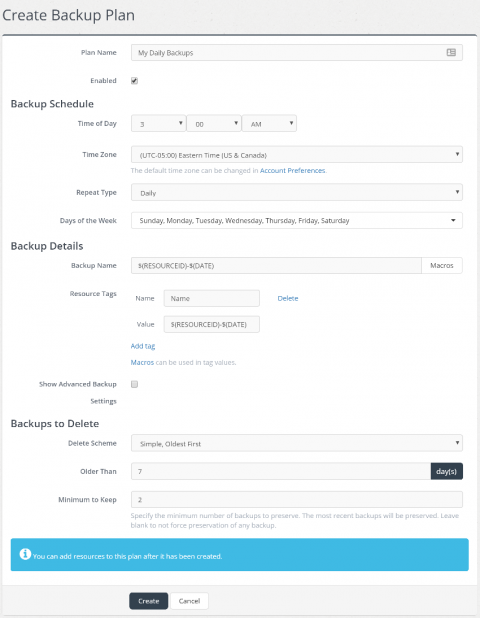
Grafana v6.4 Released
Grafana 6.4 comes with a lot of new features and enhancements backed with tons of work around the data models and query execution that is going to enable powerful future capabilities. Some of those new capabilities can already be seen in this release, like sharing query results between panels.