Operations | Monitoring | ITSM | DevOps | Cloud
%term
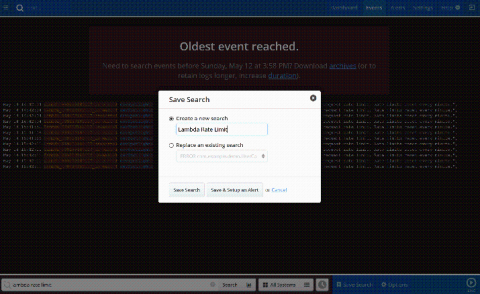
ServiceNow And PagerDuty: Choose Your Own Adventure!
Welcome, Yangstas! (Can I call you folks that? What are Yangstas? YOU! I’m Lisa Yang. Get it?) I’m excited to take you folks on a new type of journey today! But first, go give Setting Up Your PagerDuty for Sweet Victory a quick read if you haven’t read it already, it’ll give you some context around PagerDuty setup on its own.
Whats New on Statuspal 2.15
It’s been some months since we last wrote about Statuspal new features, but that’s not because we haven’t been hard at work, quite the opposite, we have delivered plenty of new features that our customers are already loving, here is a summary of the most important ones.
What is Database Security?
Database security refers to the various measures organizations take to ensure their databases are protected from internal and external threats. Database security includes protecting the database itself, the data it contains, its database management system, and the various applications that access it. Organizations must secure databases from deliberate attacks such as cyber security threats, as well as the misuse of data and databases from those who can access them.
The key to multi-cloud success
In the era of cloud-based architectures, companies have implemented multiple cloud platforms but have yet to reap the full benefits. Whether it’s Amazon Web Services (AWS), Google Cloud, or Microsoft Azure (or some combination thereof), a recent Forrester study found that nearly 86 percent of enterprises have incorporated a multi-cloud strategy.
Deploying a serverless data processing workflow with AWS Step Functions
This is the first of a two-part blog series. In this post we’ll use Stackery to configure and deploy a serverless data processing architecture that utilizes AWS Step Functions to coordinate multiple steps within a workflow. In the next post we’ll expand this architecture with additional workflow logic to highlight techniques for increasing resiliency and reliability.
Are You Ready For Serverless Development?
The way we build software products changes all the time. Serverless architecture opens up new opportunities to create awesome products faster. Not only that, serverless applications are more scalable, secure and maintainable – all with much less code. Serverless is the future of development and you should get ready for it. But what does it mean to be a serverless developer? What do you need to understand before jumping into the serverless pool?
The Super Bowl Of The Cloud
On February 3, 2019, the Sumo Logic platform experienced its biggest ever spike in incoming data and analytics usage in the company’s history. On this day, close to everybody in the U.S., and many more people across the world, experienced a massive sports event: Super Bowl LIII. The spike was caused by viewers across the world tuning into the football game using online streaming video.
ITOps vs. DevOps: What Is the Difference?
ITOps vs. DevOps: where does one end and the other begin? These two terms are commonly confused even within the IT industry, which is understandable since neither is set in stone and they often overlap, especially when talking about infrastructure. What does each role encompass and how can you tell the difference between them?