Operations | Monitoring | ITSM | DevOps | Cloud
Compliance
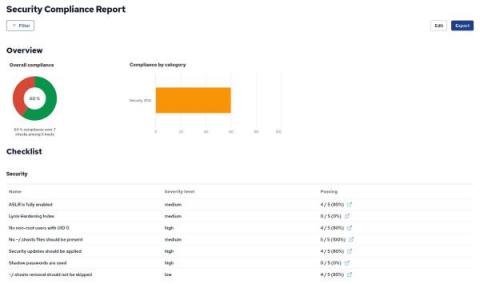
Building a Compliance Report based on inventory modules
In CFEngine Enterprise we collect information from each system in the infrastructure as inventory. Some inventory is available by default, and more can be added using modules or writing policy. You can use inventory information to create a Compliance Report with checks that determine if the information complies with your security requirements. In this blog post, we will use some modules from CFEngine Build which provide inventory data, and build a Compliance Report on top of those.
Top 5 Invoicing Trends That Will Shape The Online World In 2023
5 Ways to Keep up with Changing Compliance
Broadcom's Rally Software Receives FedRAMP Authorization For Value Stream Management Solution
Puppet supports DoD continuous compliance and configuration management
Puppet Enterprise now offers Compliance Enforcement Modules aligned to DISA STIGs Benchmarks. The Defense Information Systems Agency (DISA) Security Technical Implementation Guides (STIGs) were built to safeguard our most critical security systems and data against a dynamic threat environment, yet monitoring and enforcing widely deployed infrastructure at the U.S. Department of Defense (DoD) scale is a formidable task.
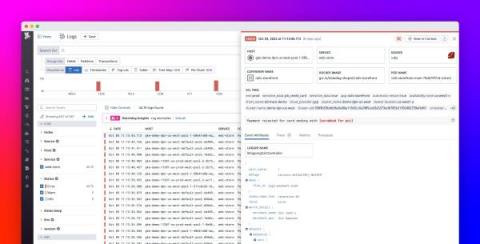
Announcing PCI-Compliant Log Management and APM from Datadog
For any organization that stores, processes, or transmits cardholder data, monitoring can pose a particular set of challenges. The Payment Card Industry (PCI) Data Security Standard (DSS) dictates rigorous monitoring and data security requirements for the cardholder data environments (CDEs) of all merchants, service providers, and financial institutions.
Monitoring Transaction Log Files for PCI compliance
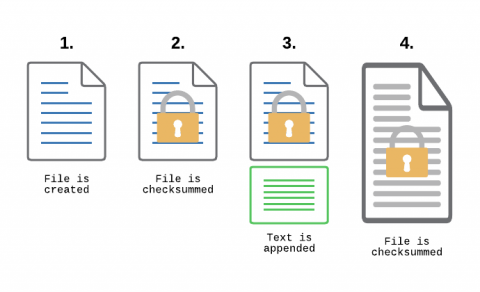
File Integrity Monitoring, aka as FIM, is a must-have feature for anyone in charge of security. With FIM, one can detect when a critical file, such as a file that belongs to the Operating System, or a key configuration file, is changed. In most cases, configuring FIM is straightforward: If the file changes then generate an alert.
Internal Social Media Platforms and Risk Management
Top 5 Ways MSPs Can Focus on Network Compliance to Boost Revenue
The barriers of entry in the service provider industry have come down-causing the MSP market to grow by nearly 33% last year and reaching nearly $355 billion by 2026.