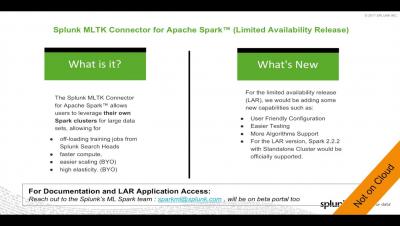
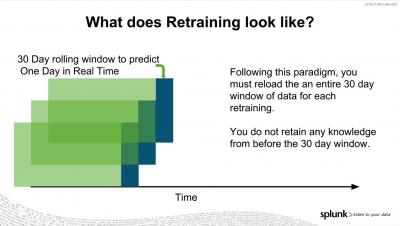
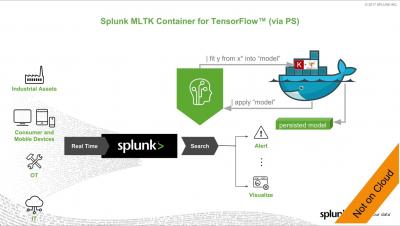
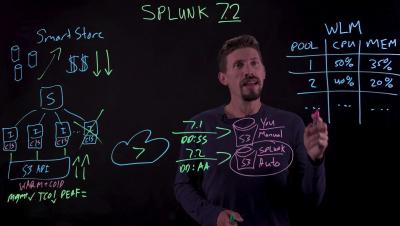
Machine Learning with AWS Lambda
We all know the latest trend in today’s technology and how Machine Learning is changing the way business decisions are made. Machine learning replaces old manual repeatable processes and provides the systems the ability to get into a mode of self-learning without being explicitly programmed.