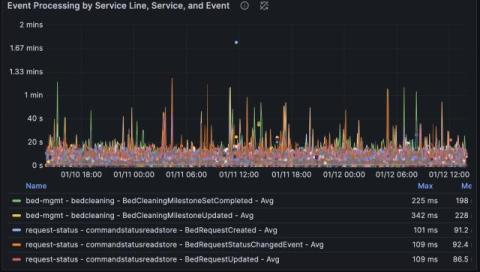
Aiven's Vision for Enterprise Solutions and Sustainability
At the forefront of everything we do at Aiven, is our customers. And we do this by focusing on enterprise readiness, trust, and compliance, bringing AI closer to daily operations, and allowing customers to leverage their existing cloud agreements.