Operations | Monitoring | ITSM | DevOps | Cloud
Analytics
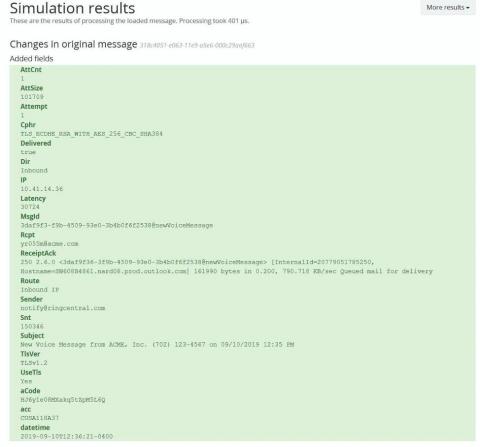
Key Value Parser Delivers Useful Information Fast
Parsers make it easier to dig deep into your data to get every byte of useful information you need to support the business. They tell Graylog how to decode the log messages that come in from a source, which is anything in your infrastructure that generates log messages (e.g., a router, switch, web firewall, security device, Linux server, windows server, an application, telephone system and so on).
What Is User Activity Monitoring? Learn the What, Why, and How
What do you think is the most important aspect of a company? Performance? Perhaps you’re thinking of profits. True, performance and profits are crucial. But security tops the list. Every company caters to different users regularly. But does the necessity of security change whether the user base is narrow or wide? Users have access to a lot of information, and often, this leads to the risk of unauthorized access and data breach.
Hunting COVID Themed Attacks With IOCs
This blog post is part twenty-four of the "Hunting with Splunk: The Basics" series. I've been dealing with viruses for years, but this is the first time I've written a blog post where we are dealing with actual viruses. Ever since the 2004 tsunami, I have witnessed cyber-baddies using current events to trick users into opening documents or clicking on links. The COVID-19 breakout is no different.
Ingram Micro chooses Elastic to bolster search, sales on ecommerce site
Ingram Micro is a Fortune 100 company with $50 billion plus in revenue and operating in 56 countries. As the global leader in delivering technology and supply chain services to businesses, Ingram Micro touches about 80% of all high tech products sold around the world. Andre Dykhno, Head of Product for Global ecommerce, says ecommerce has been a large contributing factor to Ingram Micro’s modern day successes.
Splunk Rapid Adoption Packages - Part 2
In part 1 of the RAP blog we focused on an overview of Rapid Adoption Packages, Part 2 will now focus on the use case package specifics and how these can help with customer goals. With Rapid Adoption Packages Customers have the option to select a number of use cases which are specifically designed exactly to do this, there are currently 9 available use case packages and they include...
Monitoring Family Pickle Consumption with Splunk!
Recently, about a month after our public health crisis started in the US, I opened my mailbox. Inside was a printed public service announcement sent from the mayor of my little community northwest of Denver. It had cute graphics of cartoonish townsfolk wearing facemasks, and the content conveyed reasonable, folksy messaging about social distancing and sheltering in place.
Fraud Detection: WFH Leading to Increased BEC and Phishing Threats - What To Look For
A lot has changed in the past few weeks. And the percentage of us working from home (WFH) has increased tremendously. With increased WFH, we rely more on email communication, and this increases the opportunities for abuse by others. One thing that has stayed constant: bad people want to do bad things. As we have seen in the past, when one avenue of attack is restricted, the fraudsters redouble their efforts in other areas, and online fraud attempts are already increasing during our new normal.
What Is Fault Management? A Definition & Introductory Guide
All you telecom engineers out there must have already heard of fault management, right? Well, those of you who haven’t yet heard of it and need to understand what it’s about, worry no more! I’ll help you. Let’s start by defining the term.
InfluxDB is Now Available in Google Cloud Marketplace
In February, we announced the general availability of InfluxDB on Google Cloud, as well as a rich set of integrations that allow you to use our time series data platform to monitor your Google Cloud services, store sensor data from Google IoT core, and send your time series data to Pub/Sub for analysis on Google AI Platform.