Operations | Monitoring | ITSM | DevOps | Cloud
API
The latest News and Information on API Development, Management, Monitoring, and related technologies.
Documenting your APIs with developer API portals
Autoscaling Checkly Agents with KEDA in Kubernetes
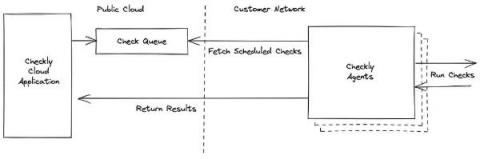
Checkly private locations enable you to run browser and API checks from within your own infrastructure. This requires one or more Checkly agents installed in your environment where they can reach your applications and our Checkly management API. You need to ensure you have enough agents installed in order to run the number of checks configured in the location. We have a guide to planning for redundancy and scaling in our documentation.
GitHub Sync goes GA
Checkly GitHub Sync Goes into GA
Welcome to the last day of our first Checkly Launch Week! We already talked about security, our new Playwright test runner and alert enhancements. Today, I’m delighted to announce that GitHub Sync is going into general availability (GA)! This post goes into the following topics.
We now support Playwright Test!
Security Controls - REST API - PowerShell Tutorial
Unleash the Full Power of Playwright With @playwright/test
Welcome to day three of our very first Launch Week! The last two days we shared how alerting became so much better and how we moved one level up by completing our SOC 2 Type 1 audit. Are you curious what’s next? I’ll tell you, but first let’s set the stage and look at Microsoft’s Playwright.
Checkly Completes SOC 2 Type 1 Audit
A Service Organization Control (SOC) audit is one of the most extensive tests an organization can undergo to demonstrate the ongoing maintenance of high-level information security. Today, we’re thrilled to announce that Checkly is SOC 2 Type 1 compliant after completing a successful audit by an accredited auditing firm. This demonstrates that Checkly’s information security policies, procedures, and practices meet the SOC 2 guidelines for security and data privacy.