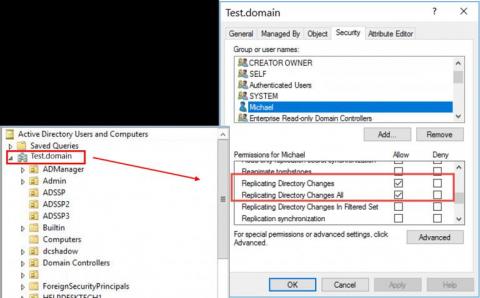
Vabi gains total visibility into its network using OpManager and Firewall Analyzer
Vabi is a Netherlands-based company that provides “real estate data in order, for everyone.” Since 1972, the company has focused on making software that calculates the performance of buildings. Nine out of 10 utility buildings in the country have been simulated with Vabi’s sustainable model. Vabi has widened its scope from making calculations for construction and installation technology to making building data accessible to everyone.