Operations | Monitoring | ITSM | DevOps | Cloud
Cyberattacks
Halloween Cyber Street- SQL injections and cross site scripting attacks
Beware of black cats and black hats this Halloween
It’s that time of the year again when you sport your favorite costume, carve pumpkins, gear up for trick-or-treating, and reread Gothic stories. It’s almost Halloween! There is no denying that October is all about ghosts and ghouls, tricks and treats, witches and wizards, pirates and pumpkins. However, October is also National Cybersecurity Awareness Month (NCSAM), a time to remember that alongside our cogent fears lies another reality that’s much more ghastly—cyberattacks.
5 Most Common Web Application Attacks and How to Defend Against Them
Globally, cybercrime was the second most reported crime in 2016, and cybercrime damages are anticipated to cost businesses and organizations $6 trillion annually by 2021. One of the ways that cybercriminals attack businesses is through the use of web application vulnerabilities. A web application vulnerability is a flaw or loophole in an application’s code that can be exploited by attackers to facilitate cybercrime. Imperva reports that web application vulnerabilities are on the rise.
Five worthy reads: Fend off cyberattacks using dark web intelligence
Five worthy reads is a regular column on five noteworthy items we’ve discovered while researching trending and timeless topics. This week, we discuss how organizations can use the dark web to build a treasure trove of actionable intelligence to prevent attacks.
USA Today Side Steps Targeted DDoS Attack with Sumo Logic
“We’re under attack” may be the three least favorite words of every cybersecurity professional out there. Luckily, for USA Today, this doesn’t happen often, however, last year one of our 115 media markets was targeted by a distributed denial of service (DDoS) attack.
Browser based attack vectors and how to protect against them
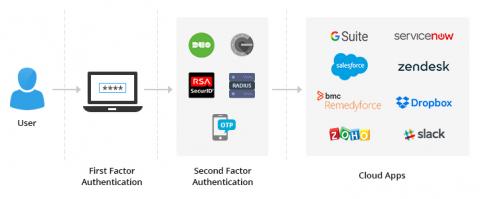
Thwart password spray attacks to secure employee access to cloud apps
Chances are you’ve heard of traditional credential-based attacks on Active Directory (AD) and cloud applications—brute force attacks, dictionary attacks, and keylogging, to name a few. There’s now another attack type you should familiarize yourself with: password spray attacks. In this blog, we’ll analyze why you should be wary of them and the best way to tackle them.
Cybersecurity Best Practices: Protect Your Team from Phishing Attacks
Phishing happens. It is probably happening as you read this. Right now, some well-defended company is having data under its care exposed. This data may contain sensitive information, such as login credentials, and in many cases, it is only known that an attack of this type has taken place after the fact. Protecting yourself and your employer against phishing attacks relies foremost on critical thinking; however, there are some business processes and technologies that can help.
Types of DNS Attacks and How Application Monitoring Can Help
DNS, the Domain Name Service, is the Internet service that translates IP addresses into hostnames, and visa versa. It enables you to type www.exoprise.com in a browser, or send an email to someone at that domain, and have your request actually go to 35.172.52.247. As a vital part of the Internet infrastructure, DNS attacks can have a serious impact on your online operations, including access to your website and email.