Integrating Threat Intelligence with Graylog
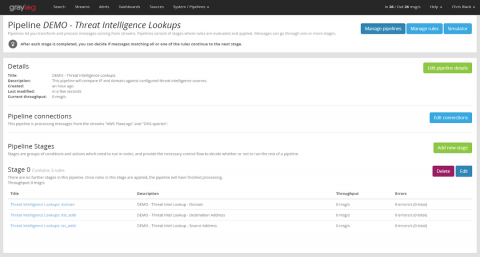
In my last post, I gave a high-level overview how to select a threat intelligence vendor and how to integrate indicators of compromise (IOCs) into your SIEM or log management environment. In this post, I will describe in detail how to use the Threat Intelligence plugin that ships with Graylog. I’ll start with the steps necessary to prepare your data, then explain how to activate the feature and how to configure it for use.