Operations | Monitoring | ITSM | DevOps | Cloud
Latest News
Kubernetes and Helm: monitoring with Prometheus and Grafana
Helm was born during the Pycon conference in 2013. Well, it wasn’t exactly Helm, it was Docker. It took Mr. Solomon Hykes a little over five minutes to completely change computing history. Ok, I admit that not everyone knows about -and uses- Docker and/or Kubernetes, but there is one fact that is undeniable: Helm in November 2019 had a million downloads and that is something important. We will see why.
Competition or Coopetition in the Persistent Storage Market?
Rancher Labs’ recent launch of Longhorn was in response to DevOps’ distress call for a cloud-native persistent storage solution for Kubernetes. At the time, industry pundit Chris Mellor posted that the company had entered into direct competition with its partners Portworx and Storage OS. A healthy dose of coopetition may be more like it.
Achieving Major Efficiencies through Migration from OpenShift to Rancher
Sometimes technology partnerships are greater than the sum of their parts. That’s the case with two Swiss companies who have come together to deliver Kubernetes solutions to their customers. VSHN is Switzerland’s leading 24/7 cloud operations partner and first Kubernetes Certified Service Provider. amazee.io is an open source container hosting provider that offers flexible solutions built for speed, security and scalability.
Running Elasticsearch, Logstash, and Kibana on Kubernetes with Helm
Kubernetes (or “K8s”) is an open-source container orchestration tool developed by Google. In this tutorial, we will be leveraging the power of Kubernetes to look at how we can overcome some of the operational challenges of working with the Elastic Stack.
Kubernetes Container Security
The National Institute of Standards and Technology (NIST) Special Publication on Container Security provides a comprehensive review of the major risks for core components of a container system. One of the most obvious objects of concern (alongside a host of other things to keep a good security professional up at night) is, of course, the containers running on your platform. Container security is obviously critical to your applications and data.
What's new in Kubernetes 1.19?
Kubernetes as a project is maturing, support has been increased from nine to 12 months, and there’s a new protocol in place to ensure a steady progress on feature development. Also, many of its new features are meant to improve the quality of life of its users, like Generic ephemeral inline volumes, or the structured logging.
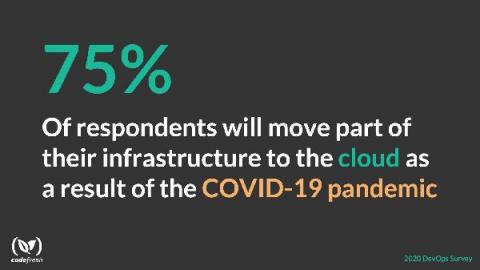
Survey Says: COVID-19 is Threatening On-prem Environments
COVID-19 is leading to large-scale migrations away from on-premises environments, according to Codefresh’s second annual State of DevOps survey that revealed this and other surprising insights into the continued evolution of the industry. At the same time, DevOps automation continues to expand in scope and complexity with more and more processes becoming automated, and more involved technologies like Kubernetes continuing to gain strong traction.
Kubevious - a Revolutionary Kubernetes Dashboard for Cross-Checking and Validating Your Kubernetes Resources
The standard Command Line Interface for Kubernetes (kubectl) is a very powerful tool for debugging or monitoring purposes. It is very inefficient, but just if you want to get a high-level overview of your Kubernetes cluster or want to work with multiple resources at the same time. A large number of graphical Kubernetes dashboards exist today and chances are that you already used the default Kubernetes dashboard or the one that comes with your cloud provider.
The Power of Open Source Software: Rancher Academy Issues 1,000th Certificate
The Rancher Academy launched on May 15, 2020. Here we are, 94 days later, and we’ve issued our 1,000th certificate to a graduate of the Certified Rancher Operator: Level 1 course. Rancher is open source software, so anyone can download it and use it. With that freedom, though, comes a cost: we all learn how to use it according to how we need to use it. Through this lens, the actual potential of Rancher becomes distorted, and the experience of each individual varies widely.