Monitor Harbor container registry with Datadog
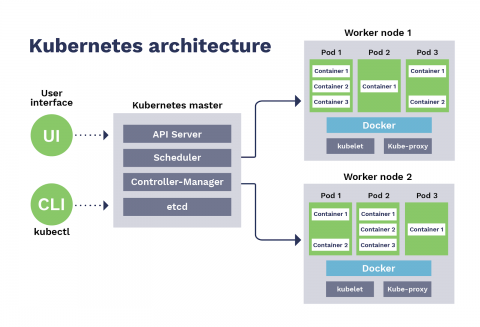
Harbor, developed by VMware and hosted by the CNCF, is an open source registry for container images and Helm charts. Hosting Harbor within your infrastructure gives you a number of advantages over using the default Docker registry, such as role-based access control, security scanning, and replication of resources between registry instances. Since a failed Harbor deployment can spell trouble for your containerized workloads, monitoring your self-hosted container registry is critical.