Securing a New Way of Working: Monitoring Those Endpoints
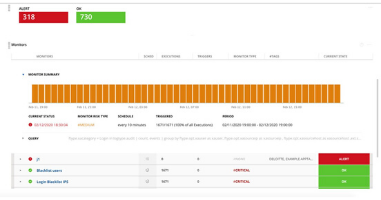
With more and more endpoints accessing your network remotely, you should expect rapid increases in VPN connections and usage, as well as exponential usage of cloud-based services. There are numerous Splunk apps that can help you increase the monitoring of remote endpoints but let’s showcase Splunk Security Essentials (SSE).