How can unifying observability and security strengthen your business?
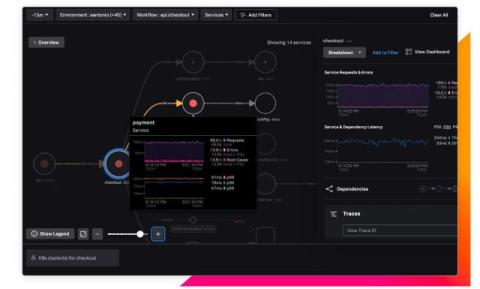
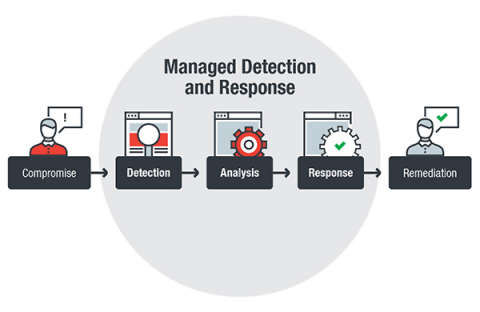
Bolster your organization’s observability and security capabilities on one platform with AI, anomaly detection, and enhanced attack discovery Organizations in today’s digital landscape are increasingly concerned about service availability and safeguarding their software from malicious tampering and compromise. The traditional security and observability tools often operate in silos, leading to fragmented views and delayed responses to incidents.