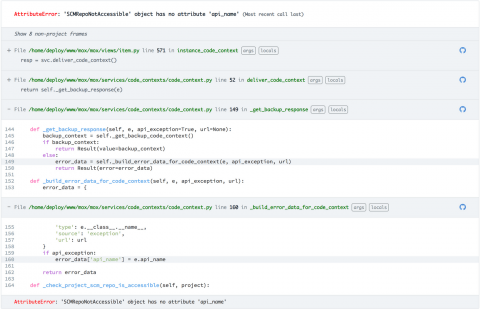
Industry best practices for endpoint security
Lately, hackers on the lookout for vulnerable systems have kept the IT industry busy. While various OS and software vendors strive to keep their users’ data intact by providing timely updates, manually securing endpoints by applying these updates is challenging due to factors such as time, staffing, and IT budgets. To help admins out, we’ve compiled a list of some industry best practices you can implement to stay vigilant against cyberattacks and data theft.