Operations | Monitoring | ITSM | DevOps | Cloud
Logging
The latest News and Information on Log Management, Log Analytics and related technologies.
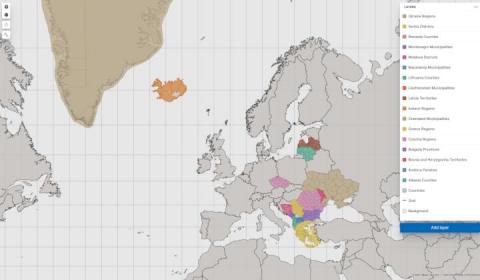
Europe regions are complete on Elastic Maps Service
At Elastic, we are adding data layers to our Maps Service on a regular basis. We are proud to announce that we have recently finished adding a number of layers that complete the European continent for all second level national boundaries. The list of new layers are Albania, Andorra, Bosnia and Herzegovina, Bulgaria, Czechia, Greece, Greenland, Iceland, Latvia, Liechtenstein, Lithuania, North Macedonia, Moldova, Montenegro, Romania, Serbia, and Ukraine.
In A Fast Changing World, Peer Benchmarks Are A GPS
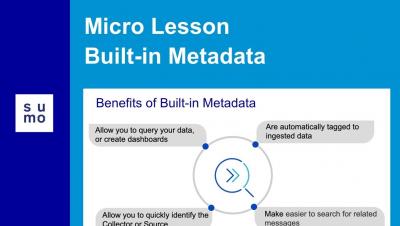
Micro Lesson: Built-in Metadata
Configuring YAML Files after Installing the ELK Stack
What is YAML? YAML is a readable data serialization language used frequently in configuration files for software; it stands for “Ain’t Markup Language.” This article will show you samples of YAML files (written .yml or .yaml) for the ELK Stack and other programs commonly used by DevOps team. And while some people love yaml and some hate it, it’s not going away.
How Do I Create A New Elastalert Rule?
When you login your stacks are displayed on the dashboard. To enable alerts for a stack, choose the 'Settings' button. Next, choose 'Alerts' and then click 'Provision ElastAlert' for this stack
Dynamic alerts
The power and value that’s embedded in logs are reflected by the status and behavior of our applications and infrastructure. Many times we would like to be alerted when the application or its components show abnormal behavior. This behavior can be reflected by the application sending some logs at a higher than usual volume. Figuring out exactly what ‘higher than usual’ means, or in other words, setting the threshold value at which the alert should trigger can be a daunting task.
[Webinar] 3 New features to enhance your website monitoring experience
A List of the Best Open Source Threat Intelligence Feeds
Threat intelligence feeds are a critical part of modern cybersecurity. Widely available online, these feeds record and track IP addresses and URLs that are associated with phishing scams, malware, bots, trojans, adware, spyware, ransomware and more. Open source threat intelligence feeds can be extremely valuable—if you use the right ones. While these collections are plentiful, there are some that are better than others.
Elastic SIEM for home and small business: SIEM overview
Hello, security enthusiasts! This is part seven (can you believe it?) of the Elastic SIEM for home and small business blog series. If you haven’t read the first six blogs in the series, you may want to before going any further. In the prerequisite blogs we created our Elasticsearch Service deployment (part 1), secured access to our cluster by restricting privileges for users and Beats (part 2), then we created an ingest pipeline for GeoIP data and reviewed our Beats configurations (part 3).