Operations | Monitoring | ITSM | DevOps | Cloud
Machine Learning
Can Data Lakes Accelerate Building ML Data Pipelines?
A common challenge in data engineering is to combine traditional data warehousing and BI reporting with experiment-driven machine learning projects. Many data scientists tend to work more with Python and ML frameworks rather than SQL. Therefore, their data needs are often different from those of data analysts. In this article, we’ll explore why having a data lake often provides tremendous help for data science use cases.
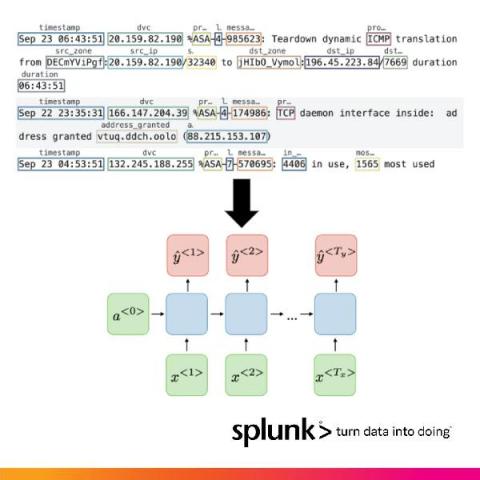
How Splunk Is Parsing Machine Logs With Machine Learning On NVIDIA's Triton and Morpheus
Large amounts of data no longer reside within siloed applications. A global workforce, combined with the growing need for data, is driving an increasingly distributed and complex attack surface that needs to be protected. Sophisticated cyberattacks can easily hide inside this data-centric world, making traditional perimeter-only security models obsolete.
Splunk Machine Learning Environments (SMLE) Labs Beta Demo
Time-based scaling of Enterprise Search on Elastic Cloud
Does your Elastic Enterprise Search Cloud deployment follow a predictable usage pattern? You can automatically scale up and down your deployment on a schedule to achieve optimal performance and reduce operating costs. In this article we show you how to use the Elastic Cloud API to change how many Enterprise Search nodes you’re running. We call these APIs from a cron job to achieve hands-free, time-triggered autoscaling.
Detecting rare and unusual processes with Elastic machine learning
In SecOps, knowing which host processes are normally executed and which are rarely seen helps cut through the noise to quickly locate potential problems or security threats. By focusing attention on rare anomalies, security teams can be more efficient when trying to detect or hunt for potential threats. Finding a process that doesn’t often run on a server can sometimes indicate innocuous activity or could be an indication of something more alarming.
AI Chihuahua: Why Machine Learning Is Dogged By Failure and Delays
AWS Machine Learning Tools (2021 edition)
When you want to stay ahead and on top of things in a fast-moving industry, machine learning (ML) is surely one of the trending solutions. Today, innovative companies already have leading Machine Learning tools well-integrated into their processes. In comparison, your start could seem dreadfully slow. Or maybe you just don’t have the time or resources to invest in running your own Machine Learning training infrastructure.
Detecting threats in AWS Cloudtrail logs using machine learning
Cloud API logs are a significant blind spot for many organizations and often factor into large-scale, publicly announced data breaches. They pose several challenges to security teams: For all of these reasons, cloud API logs are resistant to conventional threat detection and hunting techniques.
The Road to Zero Touch Goes Through Machine Learning
The telecom industry is in the midst of a massive shift to new service offerings enabled by 5G and edge computing technologies. With this digital transformation, networks and network services are becoming increasingly complex: RAN, Core and Transport are only a few of the network’s many layers and integrated components. Today’s telecom engineers are expected to handle, manage, optimize, monitor and troubleshoot multi-technology and multi-vendor networks.