Network Emulation. Bringing real-world conditions to the test environment
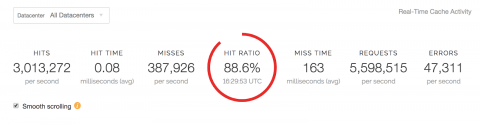
The Network Emulation is a relevant technology when making tests related to the behaviour of our platform. Let’s look at these situations: All these situations are part of the day-to-day work of the IT managers and all are responded to by developing the necessary tests. However, when we propose to do these tests, two options arise: simulation and emulation of networks. These are two concepts that are often used interchangeably but are actually very different.