Operations | Monitoring | ITSM | DevOps | Cloud
Networks
The latest News and Information on IT Networks and related technologies.
24 Best End-to-End Network Monitoring Tools for 360-Degree Network Visibility
Ribbon Launches Ribbon Connect for Zoom
What to Consider for Monitoring Network Latency
In a perfect world, data would move over the Internet in real time. There would be no delays whatsoever between when one computer sends data out over the network and when it reaches the recipient. In the real world, however, there is always some level of delay when exchanging data over the network. That delay is measured in terms of network latency. Ideally, network latency is so low that no one notices it.
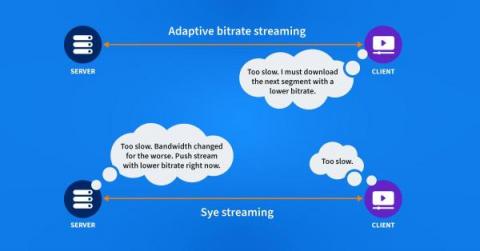
The Subtle Details of Livestreaming Prime Video with Embedded CDNs
Live sports have moved to the internet and are now streaming instead of being broadcast. Traditional streaming protocols have a built-in delay that challenges the experience of a live game. Amazon Prime has found a solution by combining a new protocol with a very distributed CDN.
Traceroute InSession: Catchpoint's effort towards a more reliable network diagnostic tool.
Since its inception in 1988, the traceroute has undergone several variations. You might be wondering, ‘Why so many?’ The answer is simple: achieving traceroute functionality has been a balance between security and utility. Whenever malicious actors exploited firewall and router vulnerabilities, their vendors responded with fixes and solutions which impacted the traceroute algorithms.
A Guide to Different Types of Network Monitoring Tools: Unveiling the Superheroes
Using Cisco Meraki Solution for SD WAN? ScienceLogic Was Built for That.
Since its acquisition by Cisco in 2012, Meraki has taken off as one of the most valuable tools for simplifying networking in the cloud era. Organizations using Meraki to install and configure software-defined networking (SDN) and software-defined wide area networking (SD-WAN) devices across their IT estates can attest to the fact.
The Power of Peer-To-Peer Networks and the Rise and Fall of Limewire
How to Achieve End-to-End Visibility Within Network Infrastructure
In March 2021, Commander of the United States Cyber Command General Paul Nakasone testified before the U.S. Senate, summarizing a key organizational challenge, "It's not that we can't connect the dots; we can't see all of the dots."