Operations | Monitoring | ITSM | DevOps | Cloud
Networks
The latest News and Information on IT Networks and related technologies.
Tackling networking issues between users and cloud apps
Common and Disastrous Network Monitoring Mistakes and How to Avoid Them
If you run a sizable enterprise, your network is probably sprawling. You also probably have a network management or IT security team on the payroll to handle monitoring. Their job is to check the network for potential security intrusions, make sure resources aren’t overloaded in one area, and otherwise ensure that things run smoothly.
7 Tips to Help Remote Workers Secure Their Home Wi-Fi
7 Tips to Help Remote Workers Secure Their Home Wi-Fi Do you remember that old song called “Dem Bones” that goes: “ankle bone is connected to the shin bone, shin bone is connected to the knee bone, knee bone is connected to the thigh bone…” and so on?
Vabi gains total visibility into its network using OpManager and Firewall Analyzer
Vabi is a Netherlands-based company that provides “real estate data in order, for everyone.” Since 1972, the company has focused on making software that calculates the performance of buildings. Nine out of 10 utility buildings in the country have been simulated with Vabi’s sustainable model. Vabi has widened its scope from making calculations for construction and installation technology to making building data accessible to everyone.
Top Three API Tips For Network Automation
Managing Network Configuration Changes Five Best Practices
Do you know what the most common cause of network outages and performance problems is? Misconfiguration. For as much time and energy as people spend talking about issues such as infrastructure and cybercrime, the truth is that basic low-level configuration challenges are still the biggest “threat” to properly-functioning networks.
Network Monitoring Just Became More Secure, Optimized, and Efficient
The entire Motadata team feels elated in informing you that Motadata Upgrade Release 7.6.400 has been rolled out and is available for installation from October 2020. We understand that many of our customers are already generating value, cost-efficiencies, and competitive edge with their existing Motadata version. But the update has been engineered to augment the entire platform’s value-proposition and making it an obvious choice for an upgrade.
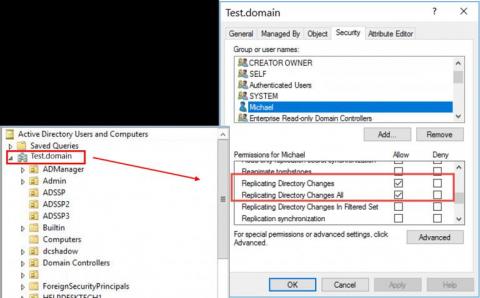
IT security under attack blog series: Instant domain persistence by registering a rogue domain controller
In this blog in the IT security under attack series, we will learn about an advanced Active Directory (AD) domain controller (DC) attack to obtain persistence in AD environments. Dubbed DCShadow, this is a late-stage kill chain attack that allows a threat actor with admin (domain or enterprise admin) credentials to leverage the replication mechanism in AD to register a rogue domain controller in order to inject backdoor changes to an AD domain.