Broadband Architecture for the Future
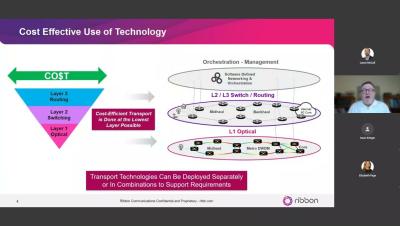
The pace of technological innovation, user demand, and the sophistication of new applications are all rapidly increasing. Will your network be able to keep up? If you build today, will the network support what your customers will require in 5 years? What about 10 years? Join us to discuss the latest developments in utilities-based middle-mile architecture and how you can confidently meet tomorrow's requirements. Learn how to create a customized and secure OT network while delivering high-revenue services to premium broadband customers.