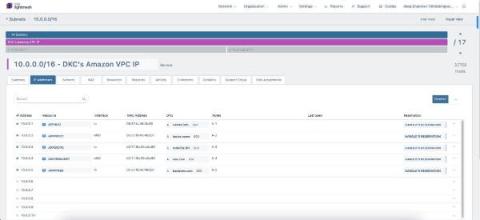
Export and Copy IP Address Data with Tidal's Enhanced Subnet Features
At Tidal, we’re always looking for ways to streamline IP address management (IPAM) tasks for our customers. That’s why we’re excited to announce the latest enhancements to our Subnet user interface (UI). With these new features, network administrators and owners can now easily export and copy IP address data, simplifying workflows and improving collaboration.