Operations | Monitoring | ITSM | DevOps | Cloud
SecOps
A day in the life of cybersecurity. Splunk customer stories of SOC-cess
We have a saying at Splunk. It goes something like “if you’re ever having a bad day, go and talk to a customer”. What organizations around the world are doing with their data and Splunk brings a huge smile and an eyebrow raising, positive “can’t quite believe you’ve done that” very-impressed nod of the head. That’s never more true than with our security customers.
Why Midsized SecOps Teams Should Consider Security Log Analytics Instead of Security and Information Event Management
ServiceNow integrates SecOps with Microsoft to boost user security
Over the past year, organizations worldwide have seen an increasing number of cyberattacks. Phishing and vulnerability exploits continue to be leading attack channels. The content adapts to the times (COVID-19-related phishing, for example), but the attack channels themselves are not new. Combating these attack types requires a focus on transforming security operations and response.
Elastic and Swimlane partner to deliver an extensible framework for the modern SOC
Today I’m happy to share more about our partnership with Swimlane, which further reinforces our commitment to empowering security teams everywhere. Today’s security teams rely on the power of Elastic’s high-speed, cloud-scale analytics to solve their most complex and pressing security issues. Swimlane’s security automation platform provides a way for these same teams to accelerate and optimize their workflows for max efficiency and to solve SOAR use cases.
Adopting a cloud first strategy for modernizing security operations
Detecting rare and unusual processes with Elastic machine learning
In SecOps, knowing which host processes are normally executed and which are rarely seen helps cut through the noise to quickly locate potential problems or security threats. By focusing attention on rare anomalies, security teams can be more efficient when trying to detect or hunt for potential threats. Finding a process that doesn’t often run on a server can sometimes indicate innocuous activity or could be an indication of something more alarming.
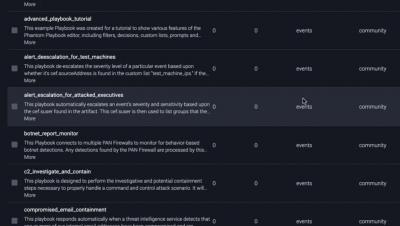
Splunk SOAR Feature Video: Playbooks
Orchestrate Framework Controls to Support Security Operations with Splunk SOAR
Every security team should utilize security frameworks in their strategy and tactics to help reduce risk from common cybersecurity threats. Security frameworks guide organizations on how they should develop, build, and maintain their IT security policies and procedures while sharing best practices for meeting compliance requirements. Healthcare operations in particular are often presented with increasing regulatory scrutiny and obligations that must be met in order to be competitive.
Security operations center, Part 3: Finding your weakest link
Any organization with data assets is a possible target for an attacker. Hackers use various forms of advanced cyberattack techniques to obtain valuable company data; in fact, a study by the University of Maryland showed that a cyberattack takes place every 39 seconds, or 2,244 times a day on average. This number has increased exponentially since the COVID-19 pandemic forced most employees to work remotely, and drastically increased the attack surface of organizations around the world.