CFEngine 3.20 released - Modularity
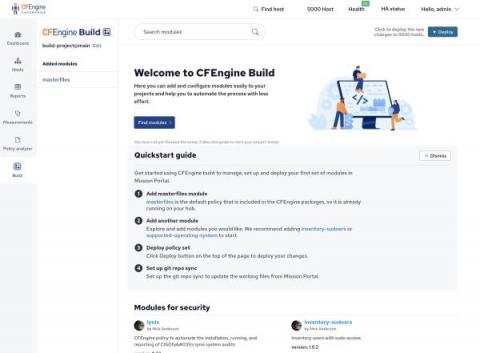
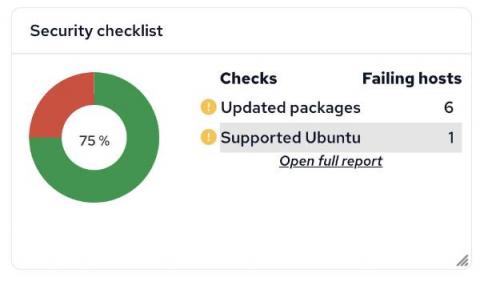
Today, we are pleased to announce the release of CFEngine 3.20.0! Over the past few years we’ve focused on ease of use, new user experience, and out of the box value, giving you the ability to do much more through only the Mission Portal Web UI. This has resulted in several important steps forward; policy analyzer, compliance reports, host specific data (CMDB), and CFEngine Build with custom promise types and other modules.